
Hello and happy Xmas/New year to you all. I recently completed a small Xss challenge at Xssmas Challenge! .I could only find 4! Give it a go!
I've spent an hour or so today investigating my eircom router. It turns out the gateway router model they use (Zyxel P-660HW-T1 v3) is riddled with vulnerabilities! I found plenty of articles explaining this and came across this gem -> Zyxel disputes vulns. There seems to be plenty of papers describing the vulnerabilities present and how they could be abused.
Anyway, I found two very useful papers that go into great detail describing the known vulnerabilities, they also wrote proof of concepts of how they can be abused. In addition to the vast array of vulns you can see in these papers below, I have found two more of my own. One is a persistent Xss and the other is Xss through a post.
Here are the articles! If you have an eircom router I recommend you give them a quick read. Hacking Zyxel Gateways part 1 and . As you can see most of these are web vulnerabilities that transfer to network vulns.
Here are my own two additional Xss vulnerabilities. The first one uses a cross site request forgery flaw on the login page to inject an xss string. This could be altered to do it automatically upon visiting a page anywhere on the internet.
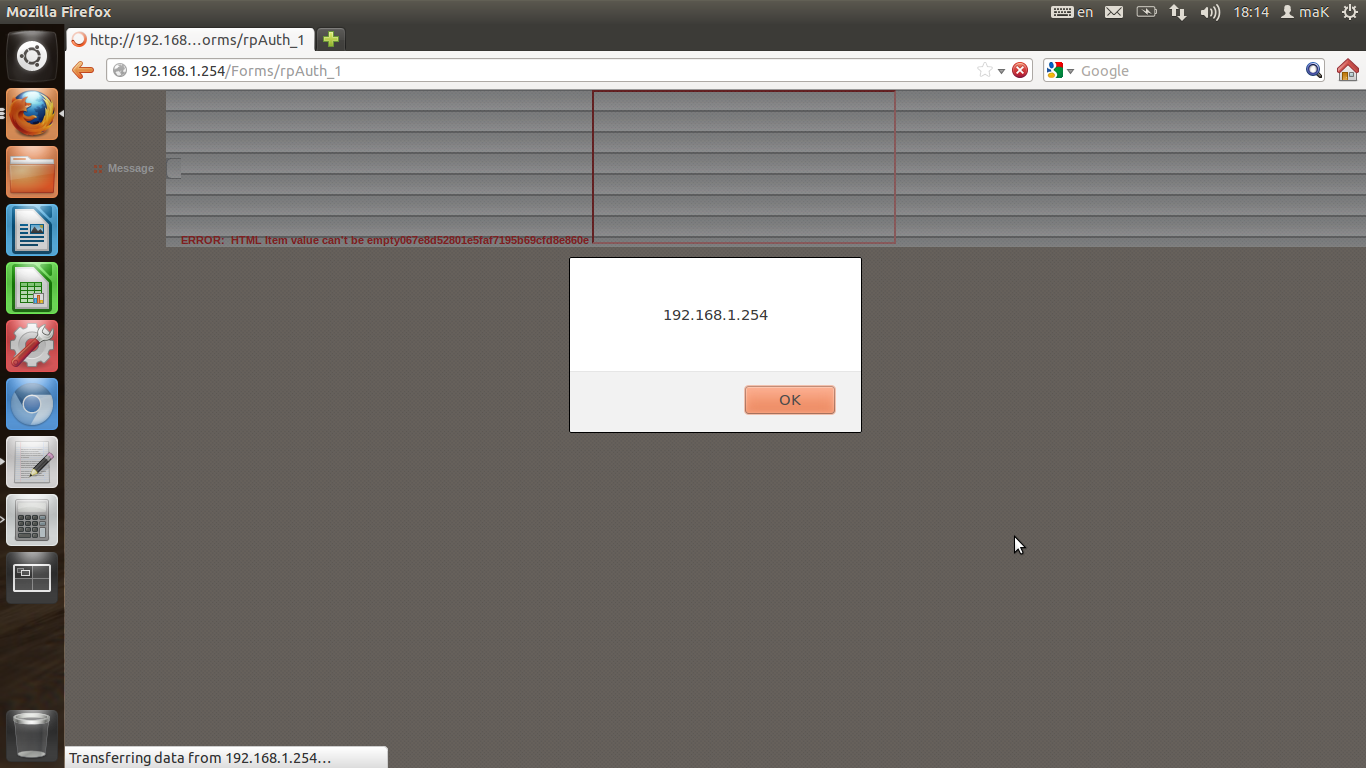
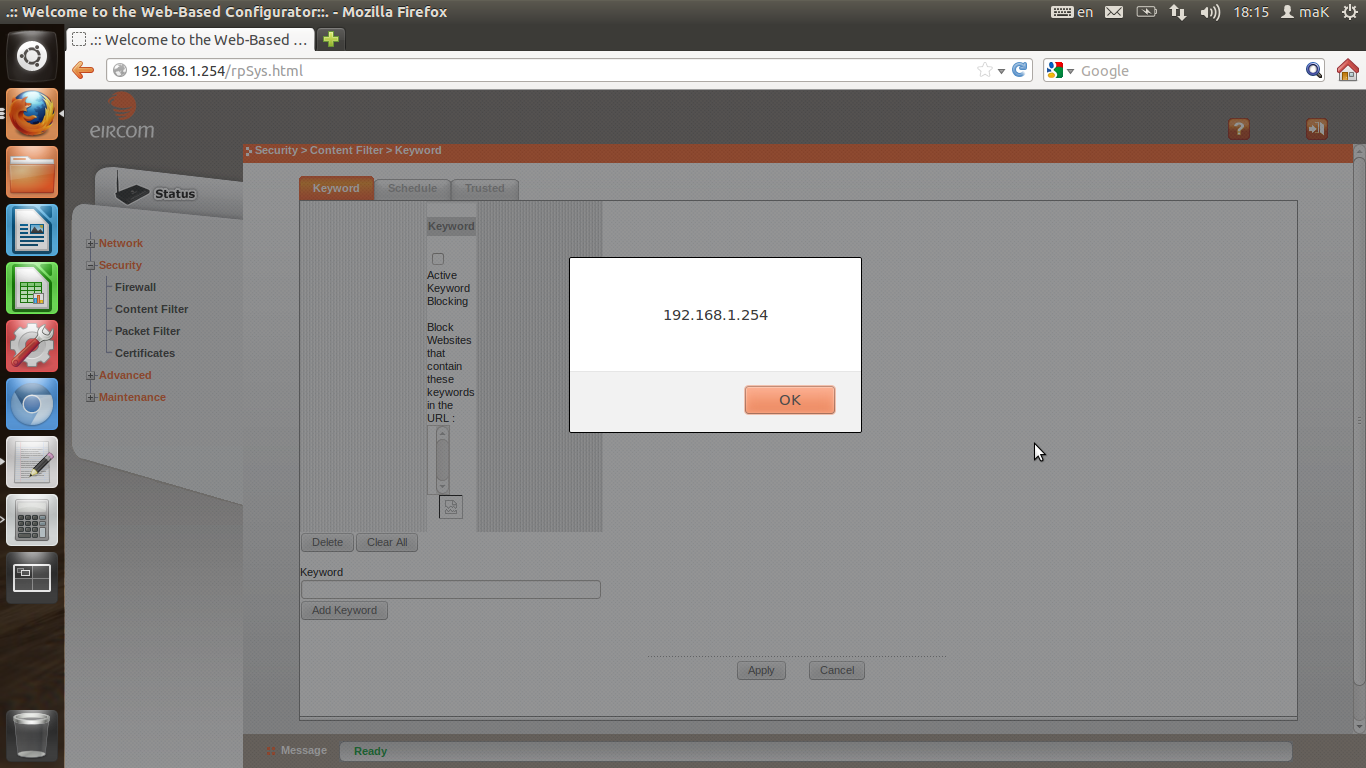
The second is a persistent vulnerability on the content filter page. If you insert a content filter keyword ofYou can store this there. This Xss could take advantage of any of the CSRF vulnerabilities described in the papers such as taking down the firewall, changing the DNS server or allowing external access to the gateway router.
I was also recently browsing a few sites with my Dom Xss finder script in an attempt to verify it actually worked and was delighted when it found a few! I reported two of the ones I found on the American Express site and was delighted with the response, they were fixed immediately. I love when a simple idea you've had works! *GLOATS*HAX BRAH